Ideal Resume Formats For 2020 [3+ Specialist Themes] Guard
Designating Permissions On Energetic Directory Furnishings
Content
Expert Driving Ability
When a new password or file is included in a Safe, each Safe participant will have their default consents on that brand-new object, as set in their Safe member authorizations. However, these permissions can be changed granularly for specific passwords or data. The Privileged Gain access to Security service gives granular accessibility control for passwords and also documents that are stored in the Vault.
Whizrt: Simulated Smart Cybersecurity Red Team
Maybe inheritance was damaged or contrasting permissions were provided. Shortcuts taken by (IT) support groups make recognizing issues in the security design application hard to monitor as well as hard to repair asap.
Include Your Contact Details The Right Way
Nevertheless, a cloned container object (a database or schema) retains any kind of benefits given on the things consisted of in the source object. As an example, a duplicated schema maintains any privileges approved on the tables, sights, UDFs, and other objects in the resource schema. By default, not even the ACCOUNTADMIN function can change or drop objects developed by a custom function. The custom role must be granted to the ACCOUNTADMIN function straight or, ideally, to another duty in a power structure with the SYSADMIN function as the parent.
They instantly inherit the access legal rights that are given to the group as well as can log in to the system immediately if new users are added to a handled team. In addition to the security profile, a set of security courses is associated with a profile. The security classes are the same across all security accounts, however each security profile has different approvals to the courses. A security class enables setting the permissions that are appointed to an instance of such a class as soon it is produced. In the editor, appoint and specify a name check out consents to a new role.
algorithm for shielding message information between a server as well as a client. Customer security concerns the authentication and confirmation of the identification of the customer based on the qualifications supplied, such as user name and also password.
What a security guard should not do?
Security guards don't normally have any legal rights beyond what a regular private citizen would have. But if they are armed and someone is a deadly threat to a client OR TO ANYONE ELSE, then they would be within their legal rights to use deadly force against the threat.
Object level accessibility enables you to regulate who can recover and make use of specific passwords and also data in the Safe, no matter Safe level member authorizations. As an example, an outside vendor or specialist can be given get or make use of authorizations for a specific password which he will be able to use without recognizing any kind of various other passwords or data in the Safe. o NEEDS TO avoid caching reactions to demands with an OSCORE alternative.
- In these circumstances, noting a team (Team A) with the Deny approval will overthrow all of its various other consents.
- So by disabling it we are taking all the access from user to see anything in stream by default.
- Giving a team the Deny approval degree amounts not noting that group within the function map, or otherwise giving them any type of authorizations.
- You can access as well as modify an existing object's security at any time by selecting the object in the application list sight, as well as picking Security in the toolbar.
- It's most beneficial in situations where a team (Team A) need to not have consents to an object yet could be embedded within an additional group that needs to have approvals to it (Group B).
Objectsecurity. The Security Policy Automation Company.
By default, user-level security is established in the embedded Oracle WebLogic Web server LDAP and Policy Store in Oracle Organisation Knowledge Business Edition. Initialization obstructs get Measurement Ids for each and every user session in order to limit row-level access to valid or dimensional data. See About Data-Level Security for a summary of the preconfigured initialization blocks.
http://b3.zcubes.com/bloghome.htm -level security - This feature is presented in Analysis Provider (SSAS) Tabular 2017. It permits you to safeguard items such as tables and columns and also it is the focus of this suggestion. Attackers replace the ID of their very own resource in the API call with an ID of a resource coming from one more individual. The absence of appropriate permission checks allows assaulters to access the defined source.
Can security guards put their hands on you?
Working as a security guard is too dangerous and that is one of the main reasons why security companies focus on proper training of the people they hire. A guard who is not properly trained will only cause frustration on the scene and also end up in trouble. The bottom line. A security guard job is extremely dangerous.
What are the 3 types of security?
The hiring manager wants to: Learn about your career goals and how this position fits into your plan. Make sure that you are sincerely interested in the job and will be motivated to perform if hired. Find out what you know about the company, industry, position (and if you took the time to research)
This attack is additionally called IDOR (Troubled Direct Object Referral). Enter the proper security level (0-- 9) for every File Access Setting (Include, Adjustment, Erase, Lookup). Any benefits approved on the source object do not transfer to the cloned object.
What should a security guard put on a resume?
Security guards should avoid making arrests, except in situations where obvious felonies are being committed. It's entirely possible that a security guard making a false arrest, or one that turns out to be unjustified, could cause your company to be sued for false arrest.

Placement power structure columns with the prefix CURRENT have the Existing Placement hierarchy at any kind of point of time. This attribute permits users to see the exact same information related to the staff member holding the Current Worker position at the time the report runs. Customers at various levels of the Placement hierarchy can use the same Position-based records yet with each user seeing the data corresponding to his or her degree.
This doesn't avoid them from making use of the ACCOUNTADMIN role to create objects, however it compels them to explicitly change their duty to ACCOUNTADMIN each time they visit. Instead, we recommend creating a pecking order of duties aligned with company features in your company as well as inevitably appointing these functions to the SYSADMIN function. For more details, see Aligning Object Access with Company Features in this topic. Intend to scan your Company Furnishings Security as well as discover your potential dangers? best methods were not followed and granular rights were appointed on content.
Security Vs. Presence
Accessibility to Oracle BI Presentation Solutions objects, such as dashboards, pages, records, and also Internet folders, is regulated using Task Responsibilities. For thorough info concerning handling object-level security in Presentation Services, see Oracle Combination Middleware Security Overview for Oracle Service Knowledge Venture Version. The security subsystem handles all kinds of consents and makes use of an advancing strategy to get to the effective approvals. You can also develop security accounts for users in the relied on domain names. Every individual is needed to have a valid security account to visit to the system.
Top 5 Skills Companies Try To Find
Security Officer Purposes
Content

There are threats and also difficulties entailed the majority of the times as the task involves safeguarding people, homes, products and so on if it's a star a security guard is protecting there are dangers of being thrashed by a mob. There are possibilities of feasible assaults if it's a politician. If it's an useful or a residential or commercial property, there is constantly the hazard of theft or robbery. Different circumstances, various obligations as well as each one with a risk of its very own.
Professional Driving Capacity
What are five hard skills?
The security features governing the security of an identity can be divided into three levels of security, i.e. Level 1 Security (L1S) (Overt), Level 2 Security (L2S) (Covert) and Level 3 Security (L3S) (Forensic).
Go through the details below, to ensure that you'll understand every little thing your security guards can and can't do on duty to make sure that they will certainly be protected, and also your company will be safeguarded. It concentrates on organizing federal, state, and also local government security officers, yet considering that May, 2000 has actually been open to standing for various other sorts of security personnel too.
Whizrt: Simulated Intelligent Cybersecurity Red Group
Unarmed security officers can still face considerable dangers, especially when they are up versus armed bad guys. This inquiry could test either your powers of observation or your biases about people. If this sort of concern is difficult for you (some individuals can not recognize faces well, for example), you must have on your own assessed in advance to make certain that you can operate as a guard. Be prepared to discuss your problem with your job interviewer. Below, to obtain you begun is a tasting of meeting concerns that you're most likely to hear during a job interview for a security personnel placement.
However it is one of one of the most high and also thrilling paying jobs today also. Yes, not every day is dangerous but there are placing your own life on the front line to secure a person or something is a huge risk on its own.
Your life is at stake most of the times as well as yet there is nothing that can be done concerning it. Security officers likewise have to maintain their physical fitness, as interfering to prevent unlawful activity may ask for physical activity. Security officers put their life on the line each time they go to work. A policeman has to challenge every hazard that presents itself.
While looking for a bullet-resistant vest for his task, Coleman attacked a female sign collector. Coleman claimed he felt "intimidated by her insistence" and also punched her in the head. New Jersey-- Since 2006 all security personnel used by a "gatekeeper company" which provides security services to other entities by agreement should undertake a state mandated certified training program. This regulation, typically described as SORA, is the state's initiative to increase the quality of security employees.
- You'll likewise need to inhabit the database with the 4 ACL-specific tables listed in the last section (refer to the ACL examples for the ideal SQL declarations).
- ACL_CLASS allows us to distinctively determine any kind of domain name object course in the system.
- Therefore, there is a solitary row for every one-of-a-kind Course we desire to store ACL permissions for.
- Compose an AccessDecisionVoter to implement the security from the GrantedAuthority [] s saved in theAuthentication object.
- You will require to include this CONTAINER to your classpath to use Spring Security's domain name object instance security capabilities.
Therefore, gatekeeper are a target for criminals that are wanting to take from, destroy, harm or otherwise perform prohibited tasks on a facility. Not all gatekeeper bear arms, nonetheless, because to do so they should initially train on just how to utilize them and also obtain pertinent accreditation and licenses.
Add Your Call Info Properly
Security personnel utilized by various other types of businesses do not need the SORA certification card. However, those used by the Atlantic City casinos are needed to have the state released "Online casino Worker Enrollment" card. Guard along with the rest of the private security industry are regulated under Act 56 of 2001, Private Security Industry Policy Act. Security Guards in Hong Kong do not have special powers of arrest above that of the man in the street, i.e. citizen's apprehension, likewise recognized locally as the "101 apprehension power". The Area 101 in the Offender Treatment Ordinance addresses that apprehension of a transgressor by a private citizen is allowed particular scenarios if the transgressor is attempting an arrestable crime.
Why is security guard important?
There are three main types of security officers working for private and public businesses and individuals: government, in-house, and those working contractually for private security firms. Within those three main types, there are even more options – armed and unarmed, plainclothes or uniformed, on-site or remote.
In terms of making apprehensions, security guards have practically the same authority as any civilian, as well as very little beyond that. Under the People Arrest provision, personal police-like guard do have the power to make an apprehension when they spot an individual dedicating a crime. It's extremely vital in such situations, though that the security guard has probable reason to arrest a person, as an example, seeing a person in the act of shoplifting.
Clients hire the agency, which gives security in the form of whichever type of guard below best fits the client's requirements. When a circumstance comes to be terrible, your security personnel will be at threat, which indicates this is a specific scenario where the authorities need to be contacted. Guard need to prevent making arrests, other than in situations where evident felonies are being committed. It's completely possible that a security personnel making an unlawful arrest, or one that ends up being unjustified, could create your company to be sued for false arrest.
The Types Of Security Guards
Relevant job experience is not necessary for finding work as a security officer but it will certainly be incredibly beneficial. Experience working in the military or police is a significant advantage. Previous experience working in a general customer-focused work or in a manual duty will also be valuable. These are the guards used contractually by exclusive security firms.
As beveiligingsbedrijf ideeën recognize what will take place next as well as when tools are entailed, things can get a lot a lot more hazardous as well as dangerous also. Although security companies focus on appropriate and also also armed forces training for their security guards sometimes along with certifications, these nevertheless can not shun risks whenever a circumstance takes place. Likewise guard do not have appropriate devices when patrolling areas at work. This implies they are frequently no match for the robbers or crooks who bring luxury arms while attempting a criminal activity.
16 Domain Name Object Security
What Are The Leading 10 Abilities That'll Obtain You A Task When You Graduate?
Content
Providing just momentary accessibility to an object by covering it in a revocable forwarder. Stopping an object from accessing one more object by never giving the initial object a reference to the second. Effective Security At the bottom of the dialog, the Effective Security, which is the security presently in use by the object, is shown. In the example over, Override (state-based or hands-on) security is in effect.
COM objects are very powerful, flexible, and also integrated with Windows, which implies that they are virtually always offered. COM items can be used to subvert various discovery patterns including command line disagreements, PowerShell logging, and also heuristic detections. Stay tuned for part 2 of this blog site collection as we will remain to take a look at hunting COM objects. Enumerating and analyzing COM objects in this fashion showed up various other fascinating finds as well.
Out-of-the-box center to enforce security based on some residential or commercial property worth is Markings. You must thoroughly research the documentation as there is some specifics and also limitations to their use. For instance, one can not have markings on a residential or commercial property with option checklist. By utilizing our site, you acknowledge that you have checked out and also understand our Cookie Plan, Personal Privacy Policy, as well as our Terms of Solution. I am explaining security rules in Basic as well as Breakthrough mode both to ensure you will not perplex just how to make regulation in both of Modes.
What are security skills?
Security guards minimize theft. Often the mere presence of a security guard will deter patrons and professionals from stealing. A guard is a greater visual deterrent than just camera surveillance or a standard security system.
Right-click on a file, thing, folder, or personalized object in Vault and also choose Details. and to obtain several data (feedback) body components in one message.
Specialist Driving Capability
as well as, because of this, would certainly not be promptly consumable by human users. encrypting trick is encrypted as well as the encrypted data encrypting secret. The retrieval might be from a local data source or from a remote service. digital signature service need to be result on precisely one line.
Whizrt: Substitute Smart Cybersecurity Red Team
How do I describe my skills on a resume?
You don't have to pull over for them, but you should, so long as you're on their property. Said security officer can make you leave property - as in, if you don't play by the rules set forth by the private property owners, you've gotta leave.
When an object inherits its security from a moms and dad object, it suggests that it shares the same function map as its parent. When this holds true, any modifications that are saved to the parent object's security role map are immediately reflected in the kid's acquired role map. Administrators - Teams who have administrative approvals to an object in a details setting. These approvals consist of the ability to fully edit or remove the object as desired. In 2017, ObjectSecurity released OpenPMF variation 4.0, that includes a new browser-based interface, cloud assistance, and also many various other features.
Add Your Get In Touch With Info The Right Way
- Doing so ensures that designers and also application individuals have the appropriate consents to the various things and features of an application.
- They do not have accessibility to Software or Overall Item.
- Analytic Workspace Supervisor produces a default policy that gives all benefits to the owner.
- Number 8-3 shows the Member Selection tab of the data security policy for PRODUCT.
- Customers that have privileges on the PRODUCT measurement based on this policy have accessibility to all Equipment items.
Mount Qlik Sense web server on your machine( Make use of a committed user as solution customer). Confirm its prerequisites and also allow it accredit then you will certainly locate two desktop computer shortcuts which are QMC and also CENTER. Please prevent alter or deletion of any default security policy in QMC. Disable problem security regulation and make a new one for screening or manufacturing usage.
What should I say in a security interview?
The skills section of your resume includes your abilities that are related to the jobs you are applying for. In this section, you should list skills that are relevant to the position or career field that you are interested in, such as computer skills, software skills, and/or language skills.

Due to the fact that reverse engineering may be needed to comprehend undocumented COM things, this is helpful. reveals all the info needed to identify COM objects, including the CLSID and ProgID. The CLSID is an around the world unique identifier associated with a COM course object.
The ProgID is a programmer-friendly string standing for an underlying CLSID. Since COM is a binary interoperability requirement, COM items are made to be applied as well as eaten from different languages. Review our electronic publication offering expert-authored stories, details, distinct insights, and also suggestions on cyber security. The very same style patterns that make code dexterous, testable, and maintainable can likewise offer security. Sandboxing an object by not providing itanyreferences outside of a small, known-safe collection.
In 2009, ObjectSecurity set up an independent legal entity in The golden state, USA to be closer to their US-based consumers. WhizRT is an intelligent automated "vulnerability assessor as well as infiltration tester" (VAPT).
The Types Of Security Guards
Supplying programmers with a Security Recap sight of each application. For inhoud van beveiligingsbedrijf , a site could have three Customer teams in its security function map. In this instance, a programmer can make use of visibility expressions on the site's pages to figure out which of these groups must and ought to not have the ability to see the pages available on the site. The complying with table details the actions of security inheritance by object kind.
What are some duties of a security guard?
A security guard is someone who patrols and inspects property against fire, theft, vandalism, terrorism, and illegal activity. They monitor people and buildings in an effort to prevent crime.
Security Vs. Presence
Regional Authentication indicates that all of the individuals exist individually in the Tableau Server. You can sync them right into the Tableau Server using the REST API. An example of using the REST API to sync users is right here. If you have some users in AD and also others that are not, make use of Local Verification, after that sync the ADVERTISEMENT individuals in through a manuscript that utilizes the REMAINDER API. When connected to Active Directory, every customer must be on a linked AD domain.
What is Things Guard Activities You Need to Use
What is Object Security Guard Activities You Required to Use
When you are an item guard, you need to have a particular sort of equipment that will help you secure your customers from harm. There are a number of types of defense that you will require to wear for you to be able to protect your clients from injury.
For instance, if you are a things security guard you will require to have a vest that will certainly help safeguard you from injury or injury while at work. This type of vest will certainly have a back plate that is made of steel to ensure that you do not have any type of mishaps while you are on responsibility.
An additional kind of vest that an object security guard ought to use is a tee shirt. You will certainly have the ability to wear this tee shirt while you are working as a things security guard so you will certainly be safeguarded from the elements and also also injury.
Obviously, another fundamental part of your clothes will certainly be your boots. hier aanmelden will require to wear boots that are constructed from rubber since these boots are mosting likely to safeguard you from injury while you are working. You likewise need to use shatterproof glass to make sure that you do not have any type of major injuries while you are working.
You might be wondering what type of protective clothes you require to put on for what is things guard activities. Right here is what you will certainly require to wear.
The next question you might have is what is object security guard tasks that you have the ability to provide for a living. The types of things that you will certainly be doing for a living will certainly rely on what sort of security personnel that you are.
You can discover several security personnel jobs that remain in the clinical area as well as others that are in the lawful field. You can also discover security personnel work that remain in the financial sector in addition to other kinds of security personnel. You can also discover security guard tasks that remain in the police and fire service.
When you are looking to be an item security personnel, you need to know what various things you will require to put on in order to secure your clients. When you recognize what you need to use you will certainly be able to select the best kind of vest as well as the ideal kind of boots to protect you.
You may additionally wish to know what is things guard activities that you can do for a living. You can pick to be a security personnel that gets on the clock for various sorts of services.
The following thing you would like to know when you are shopping for what is things guard tasks is the types of services that need you to be a security guard. You will have the ability to find security personnel that are in a resort, a club, a restaurant, a theater, a bank as well as lots of various other different kinds of organisations.
If you are a security guard that works as an outside guard after that you will be securing people that reside on your home. You will be in charge of maintaining people and also property safe.
The following point that you will certainly want to know when you are buying what is things guard activities are the kinds of services that hire you to be a guard will certainly rely on what kind of company you are seeking. You can pick a security guard position that remains in a financial institution or a restaurant or you can work as a private guard.
You will certainly have the ability to locate guard that remain in the police force along with the fire division and various other types of security guards that are in other types of security personnel. You will likewise be able to locate guard that are working with the fire and rescue solution too.

Security Personnel Return To Sample & Composing Tips
What Are The Leading 10 Skills That'll Get You A Job When You Graduate?
Content
Granting just short-lived access to an object by covering it in a revocable forwarder. Preventing an object from accessing an additional object by never offering the initial object a recommendation to the second. Reliable Security At the bottom of the dialog, the Effective Security, which is the security currently in operation by the object, is revealed. In the instance above, Bypass (manual or state-based) security is in effect.
COM items are very powerful, flexible, and incorporated with Windows, which indicates that they are nearly always readily available. COM items can be utilized to subvert different detection patterns including command line disagreements, PowerShell logging, as well as heuristic discoveries. Keep tuned for component 2 of this blog series as we will remain to consider hunting COM objects. Enumerating and also taking a look at COM items in this fashion turned up other fascinating finds too.
Out-of-the- beveiligingsbedrijf verhuurt dit to implement security based upon some building value is Markings. You need to very carefully research the documents as there is some specifics and also restrictions to their usage. As an example, one can not have markings on a property with option list. By using our site, you acknowledge that you have reviewed and also understand our Cookie Plan, Personal Privacy Plan, as well as our Regards to Solution. I am explaining security regulations in Standard and also Breakthrough mode both to be sure you will not perplex just how to make policy in both of Modes.
What are security skills?
Security guards minimize theft. Often the mere presence of a security guard will deter patrons and professionals from stealing. A guard is a greater visual deterrent than just camera surveillance or a standard security system.
Right-click on a file, folder, product, or customized object in Safe as well as select Information. as well as to receive a number of information (response) body components in one message.
Specialist Driving Capability
as well as, consequently, would not be quickly consumable by human customers. securing trick is encrypted and also the encrypted data securing secret. The retrieval might be from a local database or from a remote solution. digital trademark solution have to be outcome on specifically one line.
Whizrt: Substitute Intelligent Cybersecurity Red Team
How do I describe my skills on a resume?
You don't have to pull over for them, but you should, so long as you're on their property. Said security officer can make you leave property - as in, if you don't play by the rules set forth by the private property owners, you've gotta leave.
When an object inherits its security from a moms and dad object, it indicates that it shares the very same role map as its parent. When this holds true, any kind of adjustments that are conserved to the moms and dad object's security function map are immediately shown in the youngster's acquired role map. Administrators - Groups that have administrative authorizations to an object in a particular atmosphere. These consents consist of the ability to fully delete the object or modify as wanted. In 2017, ObjectSecurity released OpenPMF variation 4.0, that includes a new browser-based interface, cloud assistance, and countless various other features.
Include Your Contact Details The Proper Way
- Doing so guarantees that designers and also application users have the suitable approvals to the different items and functions of an application.
- They do not have access to Software or Total Item.
- Number 8-3 reveals the Member Option tab of the information security policy for PRODUCT.
- Individuals that have privileges on the PRODUCT measurement based upon this plan have access to all Equipment items.
Set up Qlik Sense server on your maker( Use a committed customer as solution user). Confirm its prerequisites as well as allow it license after that you will certainly find 2 desktop computer faster ways which are QMC and also HUB. Please prevent modify or removal of any default security policy in QMC. Disable worry security guideline and make a brand-new one for screening or manufacturing usage.
Since reverse design may be needed to understand undocumented COM things, this is valuable. reveals all the info needed to enumerate COM things, consisting of the CLSID and also ProgID. The CLSID is a worldwide special identifier associated with a COM class object.
Objectsecurity. The Security Plan Automation Company.

The ProgID is a programmer-friendly string standing for an underlying CLSID. Considering lees meer over beveiligingsbedrijf is a binary interoperability standard, COM things are designed to be implemented and also consumed from different languages. Review our digital publication supplying expert-authored tales, information, unique understandings, and advice on cyber security. The same style patterns that make code nimble, testable, and maintainable can likewise offer security. Sandboxing an object by not offering itanyreferences beyond a small, known-safe collection.
In 2009, ObjectSecurity established an independent legal entity in California, United States to be closer to their US-based clients. WhizRT is a smart automated "susceptability assessor as well as penetration tester" (VAPT).
The Kind Of Security Guards
Offering designers with a Security Summary sight of each application. For example, a site may have 3 Customer groups in its security role map. In this case, a designer can use visibility expressions on the site's web pages to determine which of these teams must as well as ought to not have the ability to see the web pages offered on the website. The adhering to table details the habits of security inheritance by object type.
What are some duties of a security guard?
A security guard is someone who patrols and inspects property against fire, theft, vandalism, terrorism, and illegal activity. They monitor people and buildings in an effort to prevent crime.
Security Vs. Exposure
Neighborhood Authentication indicates that all of the individuals exist separately in the Tableau Web server. You can sync them into the Tableau Server making use of the REST API. An example of utilizing the REST API to sync customers is here. If you have some individuals in ADVERTISEMENT and others that are not, make use of Neighborhood Verification, after that sync the ADVERTISEMENT users in by means of a script that makes use of the REST API. When connected to Active Directory, every user should be on a linked ADVERTISEMENT domain.
What is An Object Guard?
What is A Things Security Personnel?
There are several types of security personnel jobs that can execute as an item security personnel. An object security personnel is an individual that works for safety companies in the defense of a private or residential or commercial property.
As a things security guard, you are expected to keep a watchful eye on an individual or residential or commercial property, and have the ability to nab the criminal of a criminal offense. He or she works carefully with the cops division, as well as belongs to the security team of the security business.
As an item security personnel, you are anticipated to execute different guard activities that are developed to keep the general public secure. These activities include the following: seeing to it that a guard knows what is going on and what is around them, as well as making certain that security guards are correctly trained and also certified. It is the duty of this individual to recognize as well as get rid of any kind of illegal things from an area, to make sure that the area is secure, and also to report any questionable actions by an individual or a vehicle.
It is necessary to comprehend that there is a difference between an active guard as well as an inactive guard. An energetic guard will certainly be in an area that has task taking place. object beveiliging -active guard will certainly not be in a location of activity. Therefore, they are a lot less most likely to be associated with any kind of security personnel activities.
As a guard, you are not simply there to enjoy as well as take a couple of mins. The quantity of time that you exist is straight pertaining to the amount of danger that is postured by the area that you are securing. Therefore, it is essential to know the right amount of time that you need to spend on a specific area. This will certainly rely on the amount of individuals as well as the amount of property that require to be protected.
As a security personnel, you are not just operating in a location of activity. You are additionally working in a location of safety. You are called for to recognize the different methods of protecting an area. For instance, you might be required to use a fence to protect a car park. You might be required to mount an obstacle of some sort in order to secure a home or a workplace.
While you are performing your security personnel task, you are called for to use discernment. If a person is acting questionable, you should utilize caution to identify if the situation necessitates additional wondering about. You are additionally needed to have the individual recognized or gotten rid of, or jailed immediately, if you feel that further examination is required.
An object security guard is the individual that is in charge of keeping the public safe from harm as well as for every one of the various locations of an establishment. They are anticipated to understand the various methods of safeguarding any type of area that requires to be protected, and to understand exactly how to use them in the most effective manner in which is most suitable for the scenario.
The duties that a security personnel is needed to perform are a combination of things. First, they are called for to be active in the area that they are securing. Second, they are called for to be educated concerning the various types of protection and also exactly how to use them to protect the public.
The things security guard obligations are not just limited to watching and safeguarding people and their residential property. They are likewise required to be educated about various items that are considered to be a "no-no".
Things that are thought about to be a "no-no" are things like, for instance, guns, knives, or tools that can be used as tools. things that are taken into consideration to be a risk to the public, such as controlled substances, or weapons that might cause severe injury.
An object guard is required to know exactly how to safeguard these kinds of things from the general public. It is additionally required to recognize just how to act in case the public remains in danger of being hurt by them.
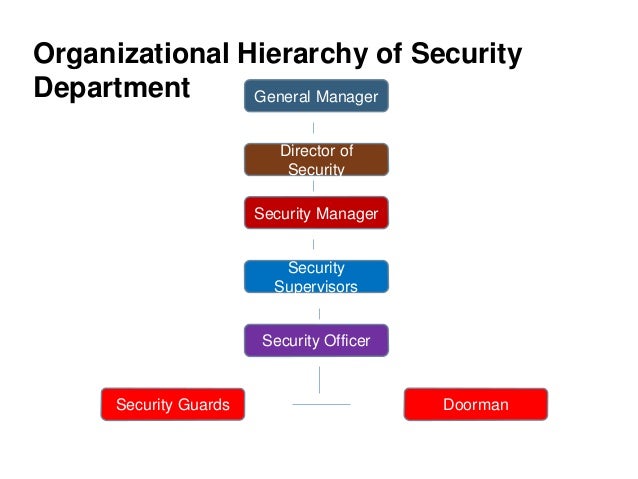
What Security Degrees Do Oracle Bi Applications Utilize?
Patents Assigned To Object Security Llc
Content
What are some duties of a security guard?
documentatie van beveiligingsbedrijf is someone who patrols and inspects property against fire, theft, vandalism, terrorism, and illegal activity. They monitor people and buildings in an effort to prevent crime.
The abilities area of your resume shows companies you have actually the capabilities required to do well in the duty. Usually, employers pay special focus to the abilities section of your resume to determine if you must carry on to the next step of the working with procedure. In this article, we check out 10 crucial skills to include on a return to, as well as tips on exactly how to finest craft the skills area of your return to.
Expert Driving Capability
Safeguard an accountable occupation possibility to completely utilize my training as well as skills, while making a considerable contribution to the success of the company. To protect a tough setting in a trustworthy company to broaden my understandings, knowledge, and also skills. Profession objective or return to unbiased acts as the pitch of your return to. This operational efficiency unbiased steps how dependable the company is when it comes to timely delivery of products to its consumers, in accordance with scheduled prices and prices.
When to utilize a return to objective to attract attention from various other candidates. A well-written career goal will certainly confirm to the employer that you're simply the candidate they have actually been awaiting. Security implies security, along with the measures taken to be safe or protected. In order to offer appropriate security for the parade, town officials commonly hire extra guards. Hardware security component-- Hardware security component that meets as well as protects economic data industry security and compliance requirements.
Whizrt: Simulated Intelligent Cybersecurity Red Group

How do I describe my skills on a resume?
You don't have to pull over for them, but you should, so long as you're on their property. Said security officer can make you leave property - as in, if you don't play by the rules set forth by the private property owners, you've gotta leave.
Micro Emphasis drives management in information security remedies with over 80 licenses and 51 years of knowledge. Web content ManagerHelping organizations meet data privacy regulative standards via the management & personality of information. Assisting organizations satisfy data privacy regulatory guidelines through the management & disposition of data. Begin by reviewing the work description as well as making note of any type of needed skills or capabilities that match your very own. In addition to job requirements, take into consideration the description of the company and also its culture.
Firms with solid security societies share the value of responsibility. By responsibility, I indicate the shared belief that each individual is ethically and also fairly bound to act responsibly for the good of his fellow employees, his company, and culture in its entirety. Till every person in your company believes this, you will certainly fight with producing a safety society. It takes more than executing a Behavior Based Security Program to transform a company's security society. Security society is greater than having procedures and measuring outcomes, it is the mindsets, ideas and worths that the entire company shares in connection to safety.
These get in touches with were established from over 30 years of experience in the private examinations as well as security market. Apart from holding a vehicle driver's permit, a bodyguard should have expert driving abilities to conserve lives and also home.
- Such systems are often both easier to make use of and much more reliable than typical security models based on globally-accessible resources shielded by accessibility control listings.
- Object-Oriented Security is the technique of utilizing common object-oriented design patterns as a mechanism for access control.
- You do not have authorization to watch this object's security homes, also as a management user.
- Where possible in this study, basic user opportunities were utilized to give understanding right into available COM things under the worst-case circumstance of having no administrative privileges.
As werkzaamheden beveiliger , it is very important to highlight your finest soft and also tough skills to position yourself as a well-shaped candidate. It's additionally valuable to consider just how the two types of skills associate with one another and also the work so you can speak with this in your following meeting. You can get expert aid with our return to responses survey if you aren't certain how to show your finest abilities on your resume.
Any individual that has actually operated in security knows that the job is not as straightforward as remaining on a feces viewing a solitary security camera screen. The "Extra Skills" section is where you get to discuss what other skills you have found out throughout the years.
Add Your Get In Touch With Details The Proper Way
Additionally, if you have a details area of proficiency, make certain to state that. If you are relating to a placement in a bank and you have experience with corporate security, you 'd definitely intend to highlight that. This security officer sample work summary can assist in your developing a task application that will attract job prospects that are qualified for the work. Feel free to change this job description to satisfy your certain job duties and also work needs. To make http://toadtights02.eklablog.com/the-responsibilities-of-an-item-guard-a197330598 of my social abilities to attain objectives of a company that concentrates on client satisfaction and also client experience.
The product's capacity to function in a desired way consistently over a sensible period of time is likewise a step of its dependability. The objective of speed procedures just how quick a company can provide its items as well as produces sales quotes. This goal will certainly be concerned with such problems as the time that it requires to make and process several items of the company or the moment that it requires to look into a new item and create it.
The Kind Of Security Guards
To produce a society that values safety and security and looking after each various other at work so everyone goes home safe, you have to concentrate on the five elements of an efficient safety society. Beau Dietl & Associates is a leading Private detective New York City Company with offices in New Jacket, Florida and also California. We have affiliates in every large city throughout the United States via our one-of-a-kind Investigations.com network. We additionally have partners worldwide in nearly every country.
Security Vs. Exposure
Knowing exactly how to drive securely, promptly, as well as successfully throughout a crisis is an experienced ability that lots of people do not have, yet the right one will. Discovering the right exec security specialist goes beyond his/her experience as well as training. Your search goes right to the core of that this individual is. The correct judgment includes assuming on one's feet and acting properly. Signs of good judgment include a calm attitude, intelligence, and vital thinking.